
Software
By now, your hardware is up and running. We’re all done, right?Not quite – now it's time to check if the software is doing what is expected of it. Before starting to troubleshoot the software side of things, it's a wise move to head over to your router configuration page and turn off all encryption on the wireless. Encryption makes a wireless network safe(r), but it also adds a layer of complexity.
Now, I'm not saying that security is a bad thing, just that it's not needed right now. We will add the encryption back later on, but let's first apply the KISS principle and try to connect without it.
So let's get to it by firing up network-admin, which can be found under System -> Administration -> Networking or by entering sudo network-admin in a terminal. Go ahead and poke around in the wireless connection. Chances are good that the wireless will connect now, but we're writing a guide for things that don't work – so it's time to go and set the parameters manually.
Drop back to a terminal and become root by issuing sudo su. First weapon of choice is ifconfig. It will show the state of all the interfaces. If the wireless interface, most likely called wlan0, isn't listed, issue ifup wlan0 and retry.
To set the parameters for the wireless connection, we'll use iwconfig. If this command is issued without arguments, it'll show a list of all interfaces and try to figure out which are wireless and with what parameters. Conveniently, iwconfig can also be used to set those parameters. For instance, to set the ESSID of the wireless network, type iwconfig wlan0 essid <ESSID>. For a very simple explanation, wlan0 is the interface of the wireless card and <ESSID> is your network's ESSID.
That's it! This should set up an association with the access point. Now, to get an IP from its DHCP server, just issue dhclient wlan0.
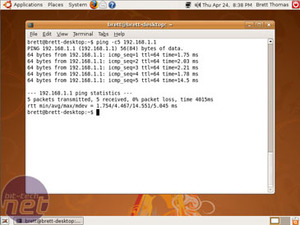 By now your wireless should be up and running. A great tool to test it is the old legend ping. Let’s start close, by pinging our router. In my case that's done by using ping 192.168.0.1. However, unlike the Windows ping tool, the Linux ping variant doesn't stop automatically after four pings. To make it stop, just press ‘<ctrl> + c’. You can avoid this by putting the -cX argument in between the command and the IP address, where X is the number of pings. So, to get the same output as Windows, you could issue ping –c4 192.168.0.1.
By now your wireless should be up and running. A great tool to test it is the old legend ping. Let’s start close, by pinging our router. In my case that's done by using ping 192.168.0.1. However, unlike the Windows ping tool, the Linux ping variant doesn't stop automatically after four pings. To make it stop, just press ‘<ctrl> + c’. You can avoid this by putting the -cX argument in between the command and the IP address, where X is the number of pings. So, to get the same output as Windows, you could issue ping –c4 192.168.0.1.If this goes fine, let's take it a bit further and try to ping something on the Internet, like ping 91.198.165.67. Since you are now a Linux wireless master, your router will work correctly and this will return good results too! Let's check that the DNS does its job as well, by issuing ping bit-tech.net.
This should do the same as the previous ping. If it doesn't, then probably the DNS nameservers aren't known to your system. Issue sudo gedit /etc/resolv.conf and check if nameserver <Router_IP> is in the file. As you might have guessed, /etc/resolv.conf holds the list of nameservers (among others). So, now that our wireless is up and running, time to add encryption!
While WEP encryption is considered pretty useless by some people because it can be cracked quite easily, it's a pretty efficient method of stopping casual war drivers that are just looking for a quick sniff around. Why waste time, how little it may be, to crack a WEP encryption when probably just down the road an open network is found?
Adding WEP encryption is easy in Linux. Remember iwconfig? Well, it can set a WEP encryption key too. iwconfig wlan0 key <secret_key> sets the key. I don't think it gets much easier than that! Of course, it isn't exactly handy to enter these settings manually every time, so we'll just save the settings in the config file. The network settings go into /etc/network/interfaces. So start to edit it by issuing sudo gedit /etc/network/interfaces and add the following under the wlan0 section:
wireless-essid <ESSID> wireless-key <secret_key>WEP may stop the lazy war driver, but some people still want a bit more encryption on their connection. WPA and WPA2 are a lot more secure than WEP, which makes them a natural choice. However, while WPA and WPA2 both work quite well on Linux, they are still relatively new implementations.
Of course, Ubuntu wouldn't be Ubuntu if some kind of GUI wasn't included. And since we have a working connection by now, just drop into Synaptic and install Network Manager. Log out and back in again and you should see the Network Manager icon. If for some reason it doesn't show, add the notifications area to your panel.
The configuration using Network Manager is straightforward and doesn't likely require an explanation. However, since WPA and WPA2 are fairly new technologies, it's worth noting that it won't work on all chipsets. Of course, if you don't fancy wasting time with experimenting, there's a list of chipsets known to work (or not to work).
Again, if yours isn't listed, go ahead and try it. Even many chipsets that had to use NDISwrapper are able to use WPA or WPA2 encryption nowadays.
Wrapping up
While this short guide is far from complete, I hope it offers some tools to troubleshoot your wireless connection in case it stops working. However, this is one of the cases where 'Google is your friend'. A quick Google with the keywords 'Linux <chipset name>' will quickly show you if your chipset works and how to get it to work.That's the power of the Linux community – and Ubuntu sure is a leader on community-driven support. The Ubuntu Forum is a prime example that Linux users aren't grumpy gits that only say ’RTFM’, although sometimes reading the manual is all it takes to solve a problem. If not, we welcome you to post your questions here in the bit-tech community, and we'll see if we can help!

MSI MPG Velox 100R Chassis Review
October 14 2021 | 15:04







Want to comment? Please log in.